In the realm of network security, VLAN attacks pose a significant threat. This guide delves into the topic of “what are three techniques for mitigating vlan attacks choose three”, exploring effective strategies to safeguard VLANs and maintain network integrity. By understanding the mechanisms of VLAN hopping, MAC address spoofing, and DHCP snooping, network administrators can implement robust countermeasures to protect their systems from these malicious attempts.
This comprehensive analysis provides a detailed examination of three proven techniques for mitigating VLAN attacks, including their advantages, limitations, and suitability for different network environments. By leveraging this knowledge, network professionals can make informed decisions to enhance their security posture and safeguard their networks from potential threats.
VLAN Hopping Mitigation Techniques
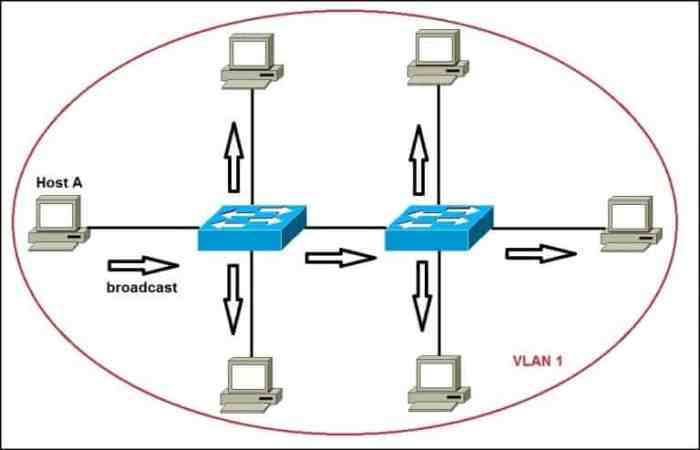
VLAN hopping refers to the unauthorized movement of attackers between virtual LANs (VLANs) to gain access to sensitive network resources. This attack can severely compromise network security, allowing attackers to intercept sensitive data, disrupt services, and launch further attacks.
VLAN Hopping Mitigation Techniques
- Port Security:This technique restricts the number of MAC addresses that can be associated with a switch port, preventing unauthorized devices from connecting to the network. It involves configuring the switch to learn and store the MAC addresses of authorized devices, and then blocking traffic from any other MAC addresses.
- VLAN Trunking Protocol (VTP):VTP is a Cisco proprietary protocol used to manage VLAN configurations across multiple switches. By disabling VTP, the network administrator can prevent unauthorized changes to VLAN configurations, making it more difficult for attackers to gain access to other VLANs.
- Access Control Lists (ACLs):ACLs can be implemented on routers or switches to restrict traffic between different VLANs. By carefully configuring ACLs, the network administrator can block unauthorized traffic from entering or leaving specific VLANs, preventing attackers from moving between VLANs.
MAC Address Spoofing Mitigation Techniques: What Are Three Techniques For Mitigating Vlan Attacks Choose Three
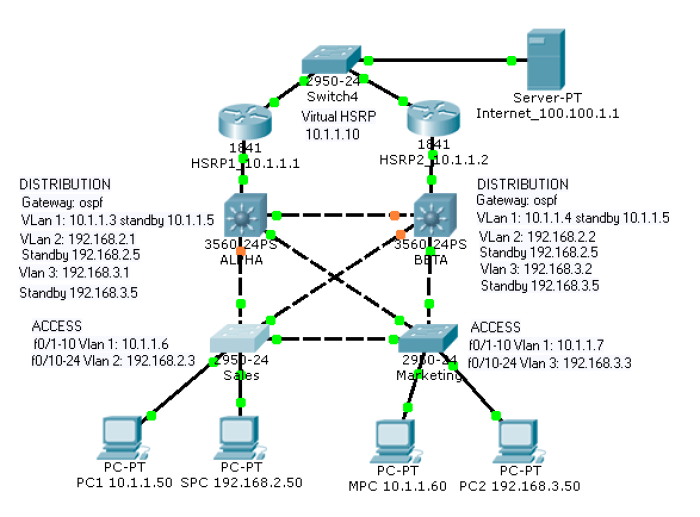
MAC address spoofing involves an attacker changing their MAC address to impersonate an authorized device on the network. This can allow the attacker to gain access to restricted VLANs and launch attacks.
MAC Address Spoofing Mitigation Techniques
- Static MAC Address Binding:This technique involves manually configuring the switch to only allow specific MAC addresses to access certain ports. By restricting the number of authorized MAC addresses, the network administrator can prevent unauthorized devices from spoofing their MAC addresses and gaining access to the network.
- DHCP Snooping:DHCP snooping is a security feature that monitors DHCP traffic on the network and validates the MAC addresses of devices requesting IP addresses. By verifying the MAC addresses, DHCP snooping can prevent unauthorized devices from obtaining IP addresses and gaining access to the network.
- 802.1X Authentication:802.1X is an authentication protocol that requires devices to authenticate themselves before they are granted access to the network. By implementing 802.1X, the network administrator can prevent unauthorized devices from connecting to the network, even if they have spoofed their MAC addresses.
DHCP Snooping Mitigation Techniques
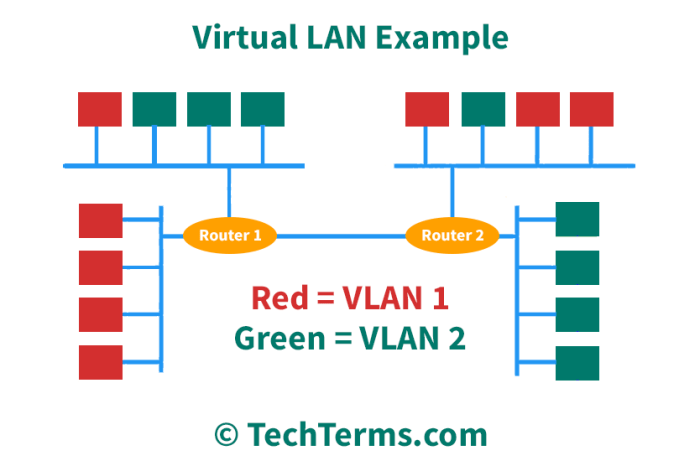
DHCP snooping is a security feature that monitors DHCP traffic on the network and validates the MAC addresses of devices requesting IP addresses. By verifying the MAC addresses, DHCP snooping can prevent unauthorized devices from obtaining IP addresses and gaining access to the network.
DHCP Snooping Mitigation Techniques, What are three techniques for mitigating vlan attacks choose three
- DHCP Snooping Binding:This technique involves configuring the switch to only allow DHCP-assigned IP addresses to be used on the network. By binding IP addresses to MAC addresses, the network administrator can prevent unauthorized devices from obtaining IP addresses and gaining access to the network.
- DHCP Snooping Trust:DHCP snooping trust involves configuring the switch to only trust DHCP servers that are located on trusted ports. By limiting the number of trusted DHCP servers, the network administrator can prevent unauthorized devices from spoofing DHCP servers and assigning IP addresses to unauthorized devices.
- DHCP Snooping Option 82:DHCP Option 82 is a DHCP option that can be used to identify the switch port that a device is connected to. By configuring the switch to use DHCP Option 82, the network administrator can track the location of devices on the network and prevent unauthorized devices from obtaining IP addresses.
FAQ
What is VLAN hopping?
VLAN hopping is a technique used by attackers to gain unauthorized access to different VLANs within a network. By exploiting vulnerabilities in network configurations, attackers can bypass security controls and move laterally across the network, accessing sensitive data or disrupting critical systems.
How can MAC address spoofing be used in VLAN attacks?
MAC address spoofing involves伪造MAC地址of a legitimate device on the network. Attackers can use this technique to gain unauthorized access to VLANs by impersonating trusted devices and bypassing access controls.
What is the role of DHCP snooping in mitigating VLAN attacks?
DHCP snooping is a security mechanism that monitors DHCP traffic on a network. By verifying the legitimacy of DHCP requests and responses, DHCP snooping can prevent attackers from spoofing DHCP servers and gaining unauthorized access to VLANs.
